How to monitor your Laravel app for critical vulnerabilities original
A critical security vulnerability was just disclosed for Livewire v3, as Stephen Rees-Carter wrote about on Securing Laravel. The vulnerability (CVE-2025-54068) allows unauthenticated attackers to achieve remote code execution in specific scenarios. What makes this particularly concerning is that exploitation doesn't require authentication or user interaction - just a component mounted and configured in a particular way.
This vulnerability affects all Livewire v3 versions up to 3.6.3. If you're running any version in that range, attackers could potentially run arbitrary PHP code on your server. Stephan warns us the open-source nature of the fix means attackers may already be reverse-engineering the patch to identify and abuse the exploit.
Many production apps are probably running vulnerable versions right now, with their developers completely unaware. This is where automated security monitoring becomes invaluable - using Laravel Health to check for vulnerabilities, and optionally services like Oh Dear to send you notifications when issues are detected.
Getting started with security monitoring using Laravel Health
You can start monitoring for security vulnerabilities in your Laravel application using the laravel-health package. This package lets you run various health checks inside your application, including checking for known security vulnerabilities in your dependencies.
First, install the required packages:
composer require spatie/laravel-health composer require spatie/security-advisories-health-check
This first one will pull in the core laravel health package
The spatie/security-advisories-health-check one, will fetch vulnerability data from the FriendsOfPHP Security Advisories database, which aggregates security advisories from GitHub and other sources. This is the same data source that powers composer audit.
Publish the configuration for laravel-health:
php artisan vendor:publish --tag="health-config"
Now create a service provider to register your health checks:
namespace App\Providers; use Illuminate\Support\ServiceProvider; use Spatie\Health\Facades\Health; use Spatie\SecurityAdvisoriesHealthCheck\SecurityAdvisoriesCheck; use Spatie\Health\Checks\Checks\UsedDiskSpaceCheck; use Spatie\Health\Checks\Checks\DatabaseCheck; class HealthCheckServiceProvider extends ServiceProvider { public function boot() { Health::checks([ // This automatically checks your composer.lock against known vulnerabilities SecurityAdvisoriesCheck::new() // While we're at it, monitor other important aspects UsedDiskSpaceCheck::new() DebugModeCheck::new(), EnvironmentCheck::new(), DatabaseCheck::new(), HorizonCheck::new(), OptimizedAppCheck::new(), ]); } }
Don't forget to register the service provider in withProviders in bootstrap/app.php.
At this point, you can already check for vulnerabilities by visiting the health check results page at /health (or by running php artisan health:check in your terminal). But manually checking defeats the purpose - you want to be notified automatically when vulnerabilities are discovered.
Add this to your app/Console/Kernel.php to ensure checks run regularly:
use Spatie\Health\Commands\RunHealthChecksCommand; protected function schedule(Schedule $schedule) { $schedule->command(RunHealthChecksCommand::class)->everyMinute(); }
This ensures vulnerabilities are detected quickly. The package also has support for sending you a notifications.
Taking it to the next level with Oh Dear
While Laravel Health does the heavy lifting of checking for vulnerabilities, you still need a way to get notified when something goes wrong. This is where Oh Dear's Application Health monitoring comes in.
Here's how it works: Laravel Health runs various checks inside your application (you can use the many available addon packages or write your own custom checks). These checks examine different aspects of your app - from security vulnerabilities to database connectivity, disk space, and more. The results of all these checks are then published on a secured JSON endpoint within your application. Oh Dear periodically reads this JSON endpoint and sends you notifications whenever something goes wrong.
This approach is particularly powerful because the checks run inside your actual production environment, giving you real-time insights into what's happening on your live servers.
Connecting to Oh Dear
In your config/health.php, enable the Oh Dear endpoint:
'oh_dear_endpoint' => [ 'enabled' => true, 'always_send_fresh_results' => true, 'secret' => env('OH_DEAR_HEALTH_CHECK_SECRET'), /* * The URL that should be configured in the Application health settings at Oh Dear. */ 'url' => '/oh-dear-health-check-results', ],
Add the secret to your .env:
OH_DEAR_HEALTH_CHECK_SECRET=your-random-secret-here
In Oh Dear's application health monitoring, add your application and set the health report URL to https://your-app.com/oh-dear-health-check-results with the same secret.
What happens when a vulnerability is detected
When Oh Dear checks your health endpoint and the
SecurityAdvisoriesCheck detects a vulnerable package (like an outdated Livewire version), you'll get an immediate notification via email, Slack, Discord, or any other channel you've configured.
I use Oh Dear myself to monitor vulnerabilities on freek.dev, and when the Livewire vulnerability was disclosed, I got an email alert that looked like this:
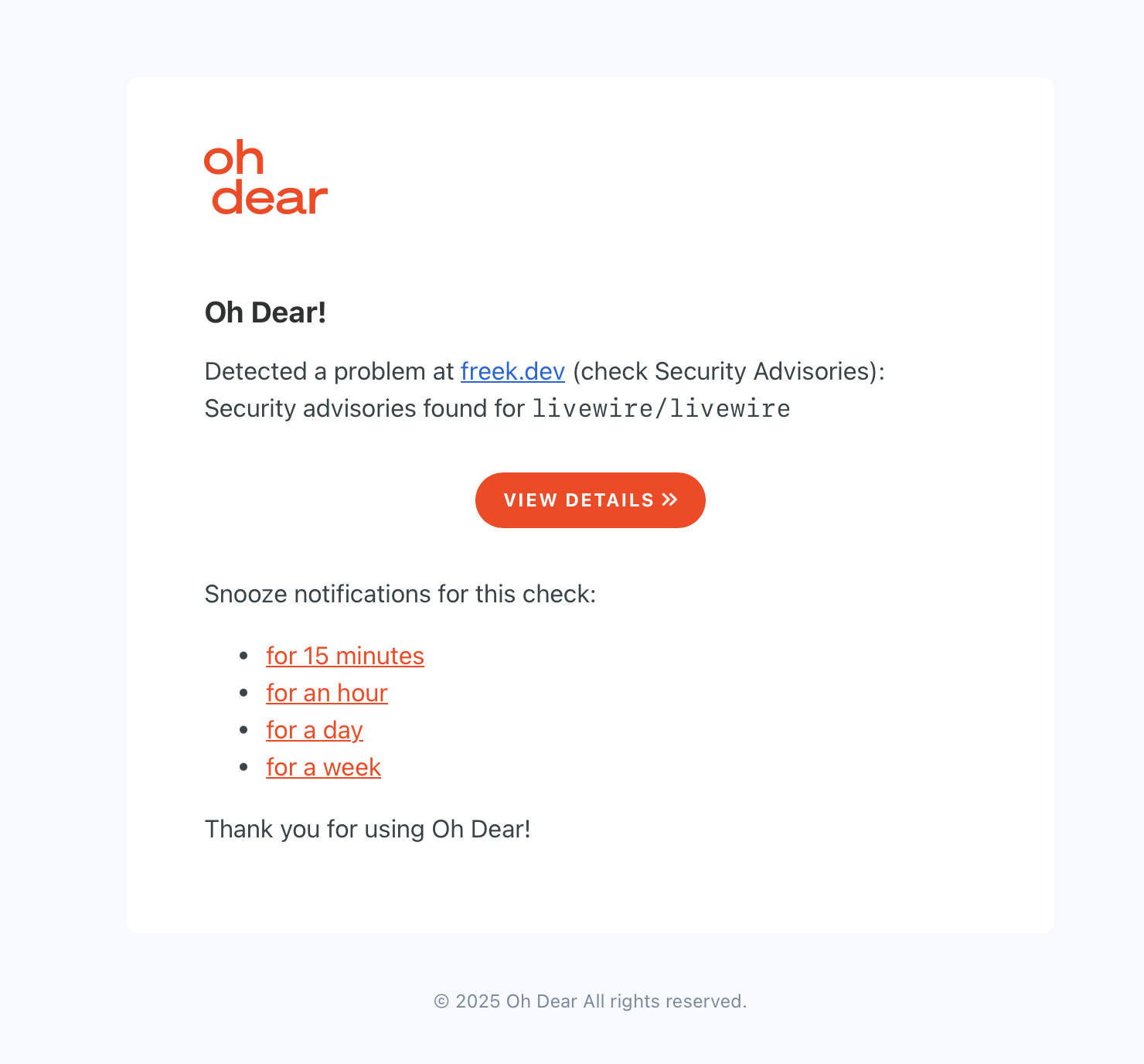
The notification clearly shows that security advisories were found for livewire/livewire. No more hoping you'll stumble upon security notices in time - the alert lands right in your inbox the moment Oh Dear detects the issue.
Here's what the JSON response from your health endpoint might look like:
{ "finishedAt": "1738879833", "checkResults": [ { "name": "SecurityAdvisories", "label": "PHP Package Security", "status": "failed", "notificationMessage": "Found 1 security vulnerability in livewire/livewire", "shortSummary": "1 vulnerability", "meta": { "vulnerabilities": [ { "package": "livewire/livewire", "version": "3.6.2", "advisories": ["CVE-2025-54068"] } ] } } ] }
Running composer audit in your CI pipeline
Here's abonus tip you can also catch vulnerabilities earlier in your development process by adding composer audit to your GitHub Actions workflow. Here's a simple workflow that checks for vulnerabilities:
name: Security Audit on: push: pull_request: schedule: - cron: '0 */6 * * *' # Every 6 hours jobs: security: runs-on: ubuntu-latest steps: - uses: actions/checkout@v4 - name: Setup PHP uses: shivammathur/setup-php@v2 with: php-version: '8.4' - name: Install dependencies run: composer install - name: Run security audit run: composer audit
This workflow will fail if any vulnerabilities are found. The scheduled run ensures you're also notified about newly discovered vulnerabilities in your existing dependencies.
In closing
The Livewire RCE vulnerability is a reminder that security threats can emerge at any time. By combining Oh Dear’s Application Health monitoring with the laravel-health package, you create an early warning system that catches vulnerabilities before they become incidents.
You might already be using GitHub's Dependabot for vulnerability scanning, which is great for repository monitoring. But there's value in also monitoring your production environment directly - Dependabot scans your repository, while Laravel Health checks what's actually deployed. This catches those cases where you've merged a security update but forgotten to deploy, or when a deployment has failed silently.
If you want to stay on top of Laravel security news and learn more about vulnerabilities like this one, I'd also recommend subscribing to Stephen Rees-Carter's Securing Laravel. He does an excellent job of breaking down security issues and explaining their impact.